An organization has identified that terminated employee accounts are not disabled or deleted within the time required by corporate policy. Unsure of the reason, the organization has decided to monitor the situation for three months to obtain more information. As a result of this decision, the risk has been:
Which of the following is the MOST appropriate action when a tolerance threshold is exceeded?
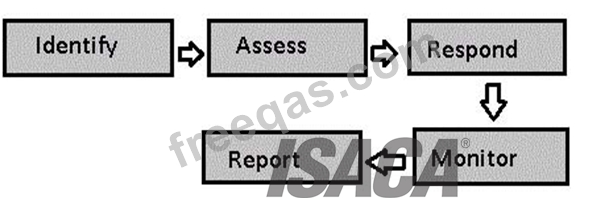
Which of the following comes under phases of risk management?
Which of the following is the final step in the policy development process?
Which of the following is the BEST method for assessing control effectiveness against technical vulnerabilities that could be exploited to compromise an information system?
