An administrator would like to see the traffic that matches the mterzone-default rule in the traffic togs What is the correct process to enable this logging1?
Assume that traffic matches a Security policy rule but the attached Security Profiles is configured to block matching traffic Which statement accurately describes how the firewall will apply an action to matching traffic?
Given the topology, which zone type should zone A and zone B to be configured with?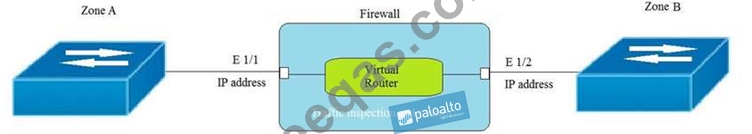
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall's signature database has been updated?
(Choose two.)
The CFO found a malware infected USB drive in the parking lot, which when inserted infected their corporate laptop the malware contacted a known command-and-control server which exfiltrating corporate data.
Which Security profile feature could have been used to prevent the communications with the command-and-control server?
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
