Based on the security policy rules shown, ssh will be allowed on which port?
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?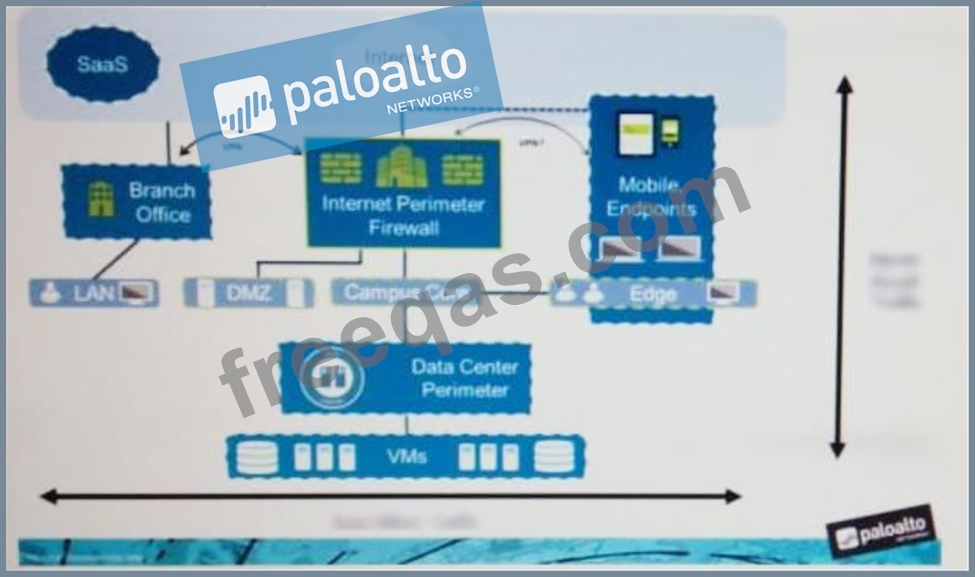
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.
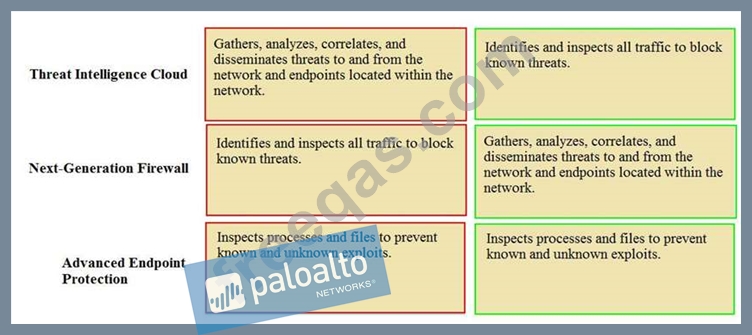
Match the Palo Alto Networks Security Operating Platform architecture to its description.
An administrator notices that protection is needed for traffic within the network due to malicious lateral movement activity. Based on the image shown, which traffic would the administrator need to monitor and block to mitigate the malicious activity?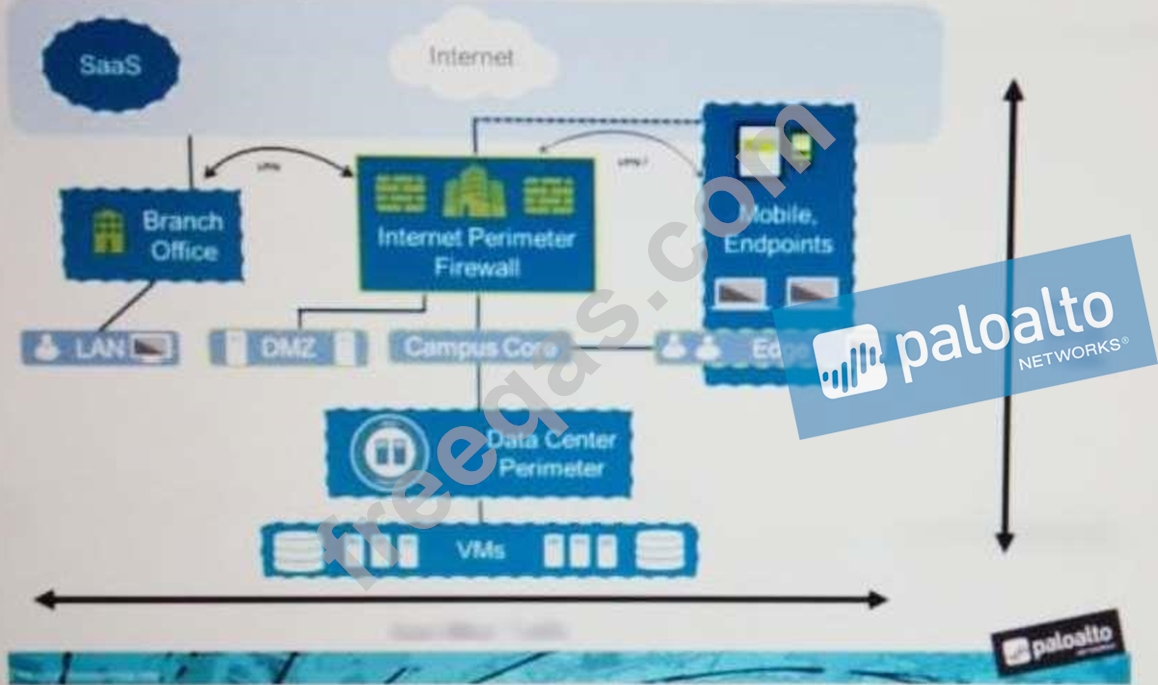
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
