Given the topology, which zone type should zone A and zone B to be configured with?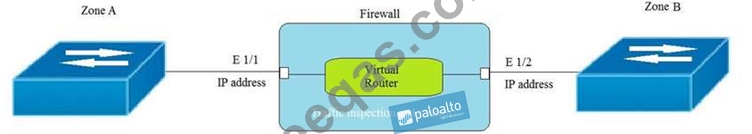
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
Which three statements describe the operation of Security policy rules and Security Profiles? (Choose three.)
Enter your email address to download PaloAltoNetworks.PCNSA.v2022-04-11.q158 Dumps
