A security analyst is reviewing the password policy for a service account that is used for a critical network service. The password policy for this account is as follows: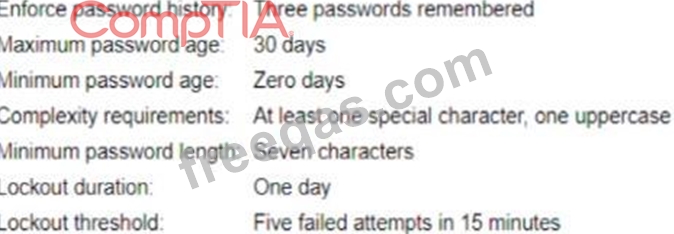
Which of the following adjustments would be the MOST appropriate for the service account?
A security analyst is attempting to identify vulnerabilities in a customer's web application without impacting the system or its dat a. Which of the following BEST describes the vulnerability scanning concept performed?
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator
accesses a workstation with the hostname of workstation01 on the network and obtains the following
output from the ipconfig command: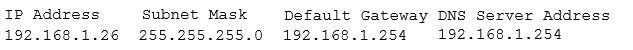
The administrator successfully pings the DNS server from the workstation. Which of the following
commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
Task: Configure the firewall (fill out the table) to allow these four rules:
Only allow the Accounting computer to have HTTPS access to the Administrative server.
Only allow the HR computer to be able to communicate with the Server 2 System over SCP.
Allow the IT computer to have access to both the Administrative Server 1 and Administrative Server 2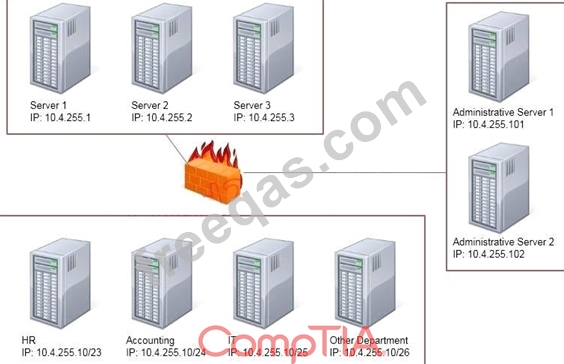

An organization plans to implement multifactor authentication techniques within the enterprise network architecture. Each authentication factor is expected to be a unique control.
Which of the following BEST describes the proper employment of multifactor authentication?
