After a recent internal breach, a company decided to regenerate and reissue all certificates used in the transmission of confidential information. The company places the greatest importance on confidentiality and non-repudiation, and decided to generate dual key pairs for each client. Which of the following BEST describes how the company will use these certificates?
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood of an incident, while the horizontal axis indicates the impact.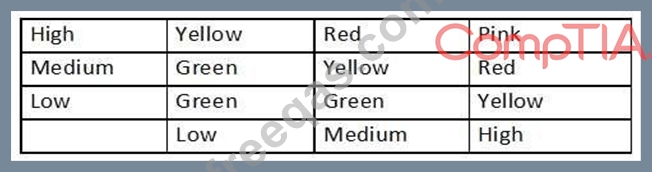
Which of the following is this table an example of?
A vulnerability scan was run multiple times. The first lime, the scan detected multiple operating system flaws The second time the scan indicated that a few third-party application programs required patching and no operating system flaws. Which of the following is the MOST likely cause tor the different scan results?
A security administrator has found a hash in the environment known to belong to malware. The administrator then finds this file to be in in the preupdate area of the OS, which indicates it was pushed from the central patch system.
File: winx86_adobe_flash_upgrade.exe
Hash: 99ac28bede43ab869b853ba62c4ea243
The administrator pulls a report from the patch management system with the following output:
Given the above outputs, which of the following MOST likely happened?
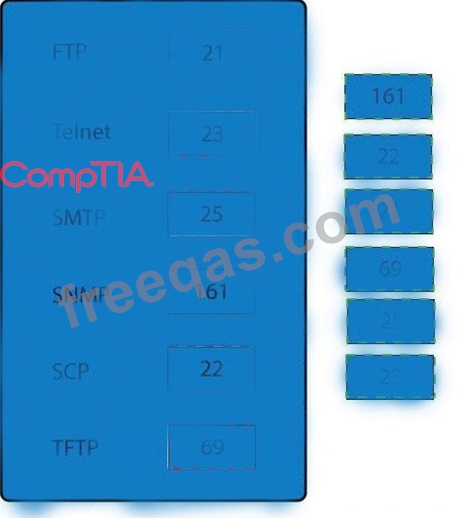
Drag and drop the correct protocol to its default port.