Which of the following is an important step to take BEFORE moving any installation packages from a test environment to production?
A home invasion occurred recently in which an intruder compromised a home network and accessed a WiFI- enabled baby monitor while the baby's parents were sleeping.
Which of the following BEST describes how the intruder accessed the monitor?
A company is implementing a tool to mask all PII when moving data from a production server to a testing server. Which of the following security techniques is the company applying?
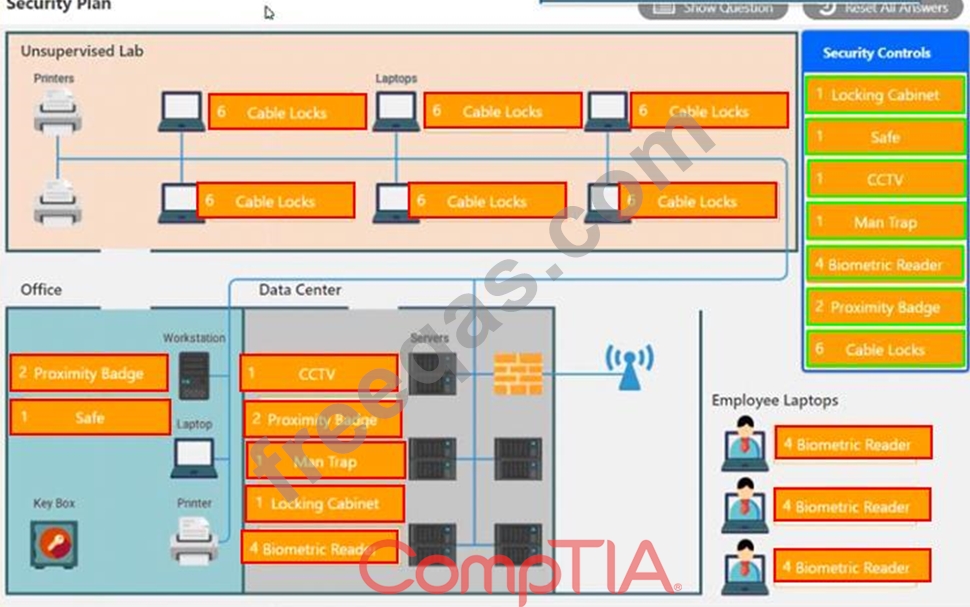
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions: All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.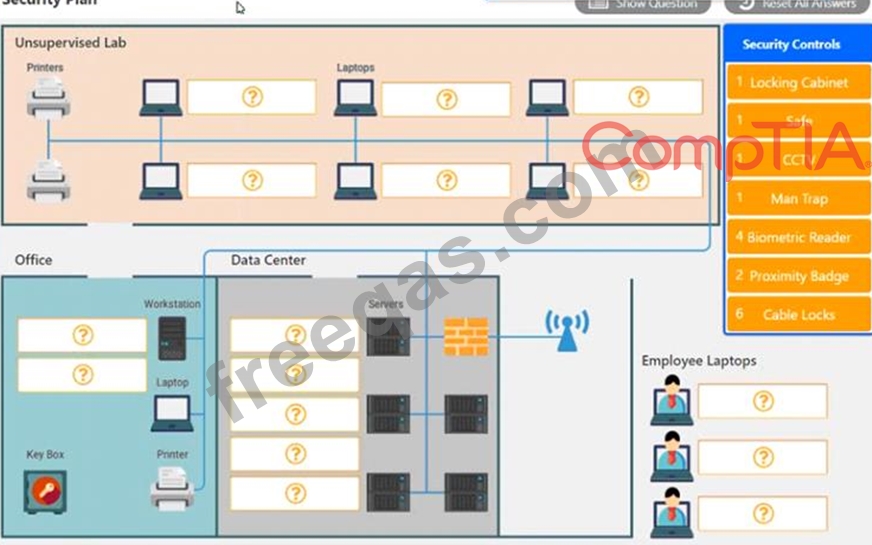
An employee of a large payroll company has a machine that recently started locking up randomly with greatly increased processor consumption Which of the following is the fiRST action an analyst should lake to investigate this potential loC?
