Security administrators attempted corrective action after a phishing attack. Users are still experiencing trouble logging in, as well as an increase in account lockouts. Users' email contacts are complaining of an increase in spam and social networking requests. Due to the large number of affected accounts, remediation must be accomplished quickly.
Which of the following actions should be taken FIRST? (Select TWO)
A security analyst discovers one of the business processes which generates 75% of the annual revenue, uses a legacy system This creates a tolerable risk that can contribute to a 2% drop in revenue generation every quarter. Which of the following would be the BEST response to this risk?
A network administrator has been alerted that web pages are experiencing long load times. After determining it is not a routing or DNS issue, the administrator logs in to the router, runs a command, and receives the following output: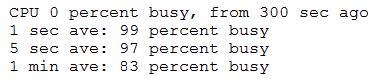
Which of the following is the router experiencing?
A hacker has a packet capture that contains:
Which of the following tools will the hacker use against this type of capture?
A wireless network has the following design requirements:
Authentication must not be dependent on enterprise directory service
It must allow background reconnection for mobile users
It must not depend on user certificates
Which of the following should be used in the design to meet the requirements? (Choose two.)
