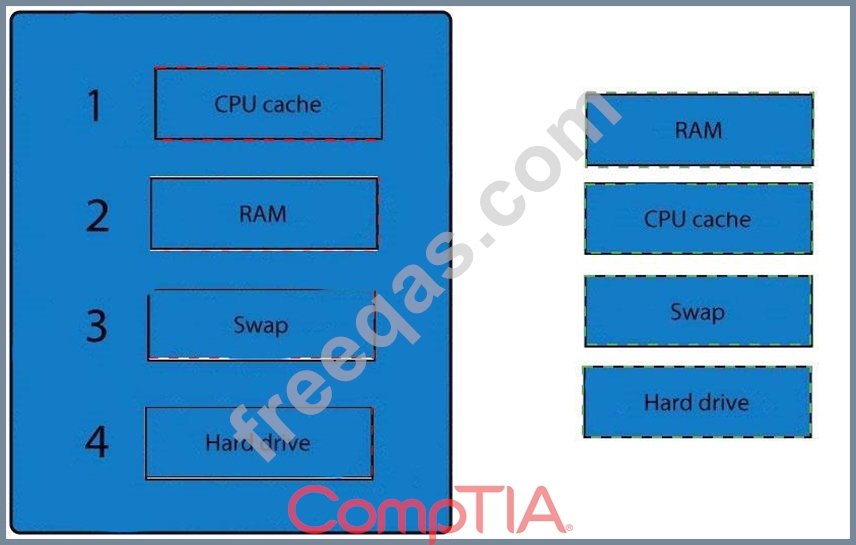
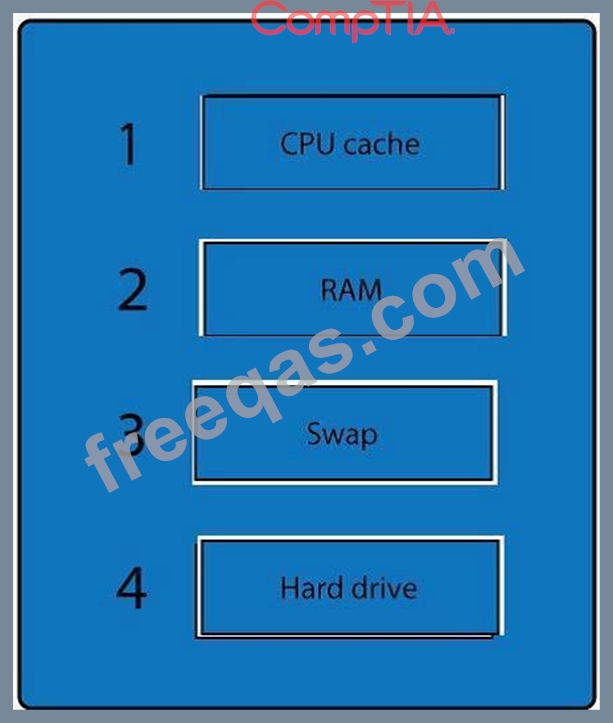
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.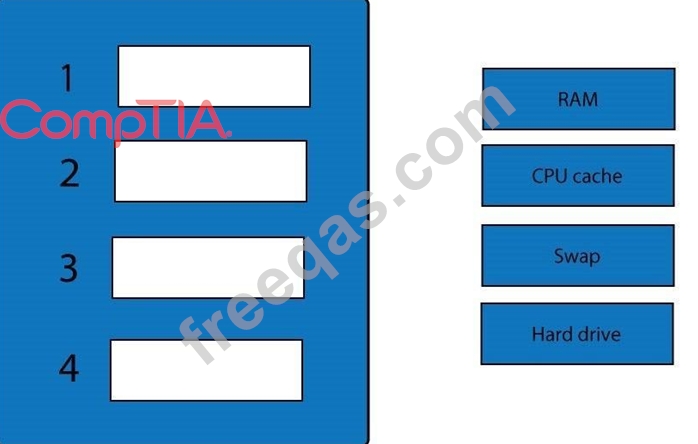
Which of the following attacks can be used to exploit a vulnerability that was created by untrained users?
Which of the following would be considered multifactor authentication?
A system's administrator has finished configuring firewall ACL to allow access to a new web server.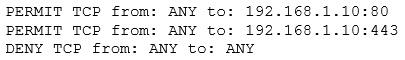
The security administrator confirms form the following packet capture that there is network traffic from the internet to the web server:
The company's internal auditor issues a security finding and requests that immediate action be taken. With which of the following is the auditor MOST concerned?
A security administrator suspects that a DDoS attack is affecting the DNS server. The administrator accesses a workstation with the hostname of workstation01 on the network and obtains the following output from the ipconfig command: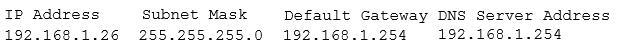
The administrator successfully pings the DNS server from the workstation. Which of the following commands should be issued from the workstation to verify the DDoS attack is no longer occuring?
