A penetration tester harvests potential usernames from a social networking site. The penetration tester then uses social engineering to attempt to obtain associated passwords to gain unauthorized access to shares on a network server. Which of the following methods is the penetration tester MOST likely using?
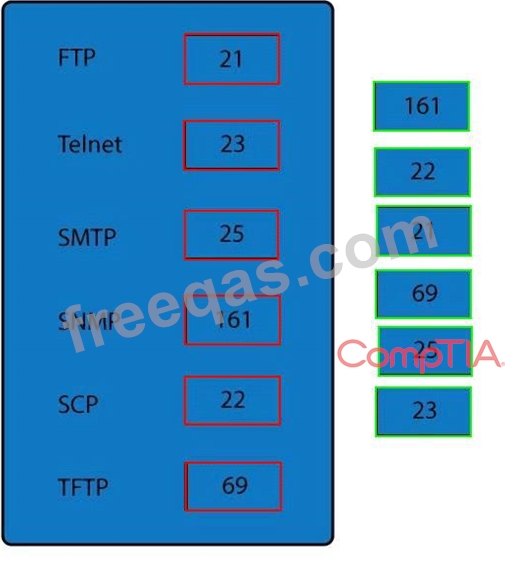
Drag and drop the correct protocol to its default port.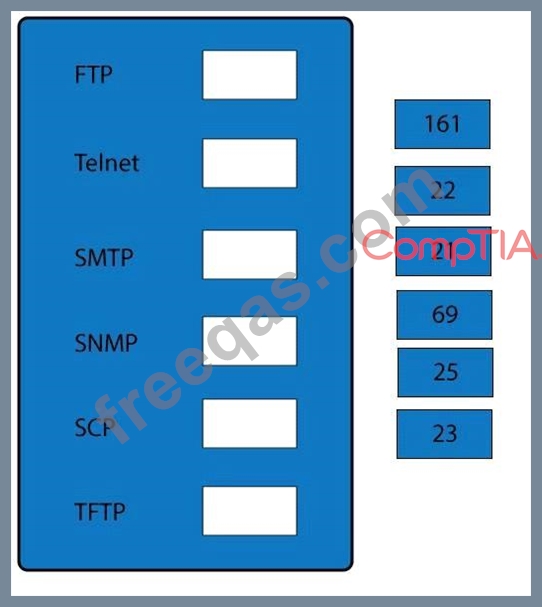
A security engineer is installing a WAF to protect the company's website from malicious web requests over SSL. Which of the following is needed to meet the objective?
Which of the following characteristics differentiate a rainbow table attack from a brute force attack? (Select
two.)
A security analyst has received the following alert snippet from the HIDS appliance:
PROTOCOL SIG SRC.PORT DST.PORT
TCP XMAS SCAN 192.168.1.1:1091 192.168.1.2:8891
TCP XMAS SCAN 192.168.1.1:649 192.168.1.2:9001
TCP XMAS SCAN 192.168.1.1:2264 192.168.1.2:6455
TCP XMAS SCAN 192.168.1.1:3464 192.168.1.2:8744
Given the above logs, which of the following is the cause of the attack?
