Which of the following characteristics differentiate a rainbow table attack from a brute force attack?
(Select two.)
The chief security officer (CSO) has reported a rise in data loss but no break-ins have occurred.
By doing which of the following would the CSO MOST likely to reduce the number of incidents?
A security auditor is reviewing the following output from file integrity monitoring software installed on a very busy server at a large service provider. The server has not been updates since it was installed. Drag and drop the log entry that identifies the first instance of server compromise.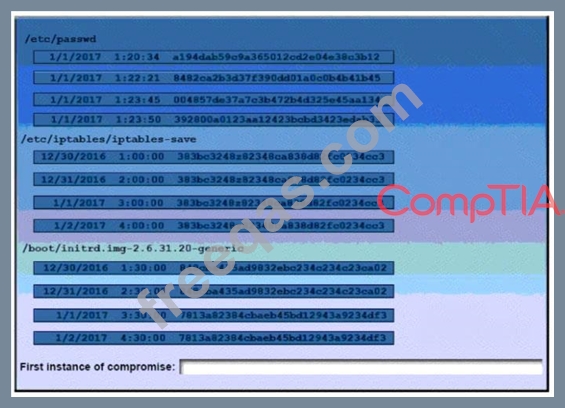
A company is deploying MFDs in its office to improve employee productivity when dealing with paperwork.
Which of the following concerns is MOST likely to be raised as a possible security issue in relation Io these devices?
The application team within a company is asking the security team to investigate why its application is slow after an upgrade. The source of the team's application is 10.13.136.9, and the destination IP is 10.17.36.5. The security analyst pulls the logs from the endpoint security software but sees nothing is being blocked. The analyst then looks at the UTM firewall logs and sees the following: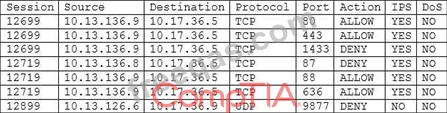
Which of the following should the security analyst request NEXT based on the UTM firewall analysis?
