A security administrator is analyzing a user report in which the computer exhibits odd network-related outages. The administrator, however, does not see any suspicious processes running. A prior technician's notes indicate the machines has been remediated twice, but the system still exhibits odd behavior. Files were deleted from the system recently. Which of the following is the MOST likely cause of this behavior?
An administrator is replacing a wireless router. The configuration of the old wireless router was not documented before it stopped functioning. The equipment connecting to the wireless network uses older legacy equipment that was manufactured prior to the release of the 802.11i standard.
Which of the following configuration options should the administrator select for the new wireless router?
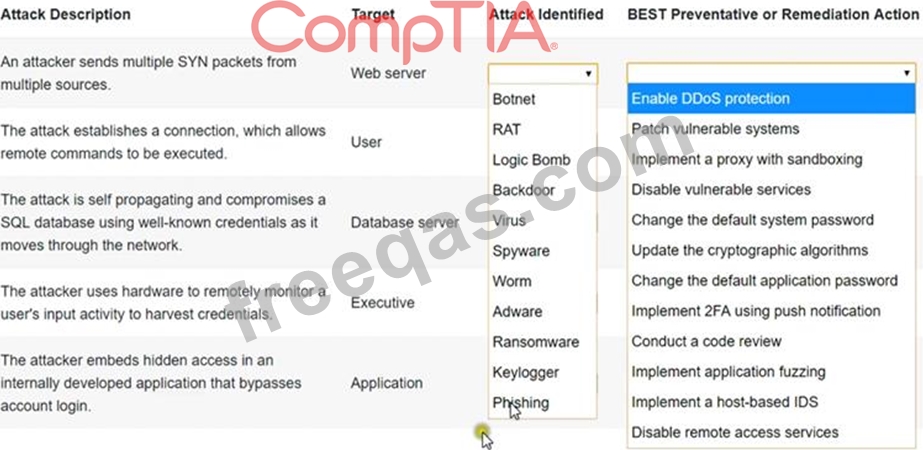
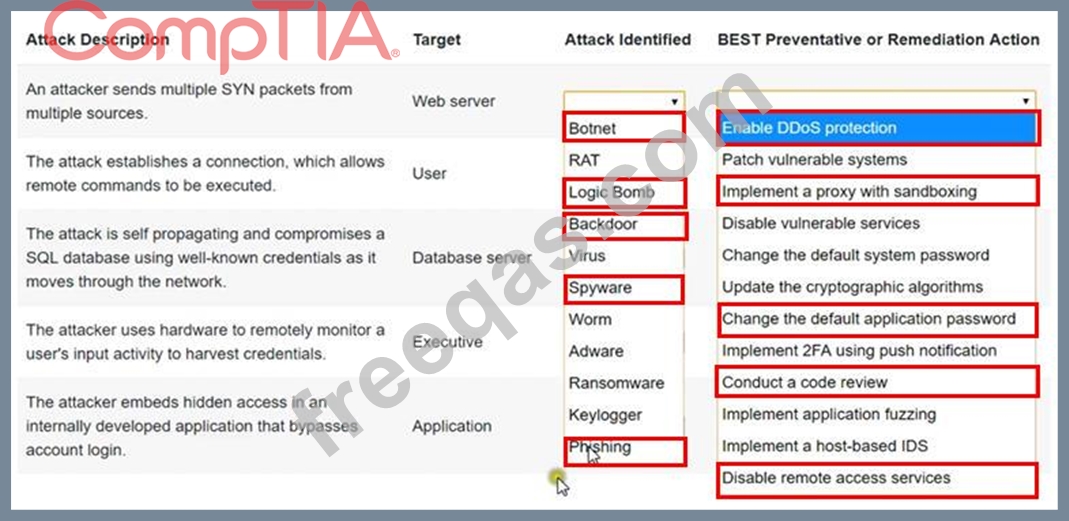
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.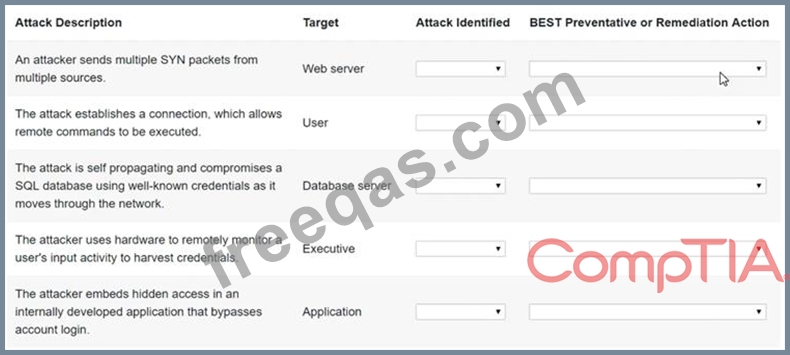
An application team is performing a load-balancing test for a critical application during off- hours and has requested access to the load balancer to review. Which servers are up without having the administrator on call. The security analyst is hesitant to give the application team full access due to other critical applications running on the road balancer.
Which of the following is the BEST solution for the security analyst to process the request?
While reviewing the monthly internet usage it is noted that there is a large spike in traffic classified as
"unknown" and does not appear to be within the bounds of the organizations Acceptable Use Policy.
Which of the following tool or technology would work BEST for obtaining more information on this traffic?
