A user suspects someone has been accessing a home network without permission by spoofing the MAC address of an authorized system. While attempting to determine if an authorized user is logged into the home network, the user reviews the wireless router, which shows the following table for systems that are currently on the home network.
Which of the following should be the NEXT step to determine if there is an unauthorized user on the network?
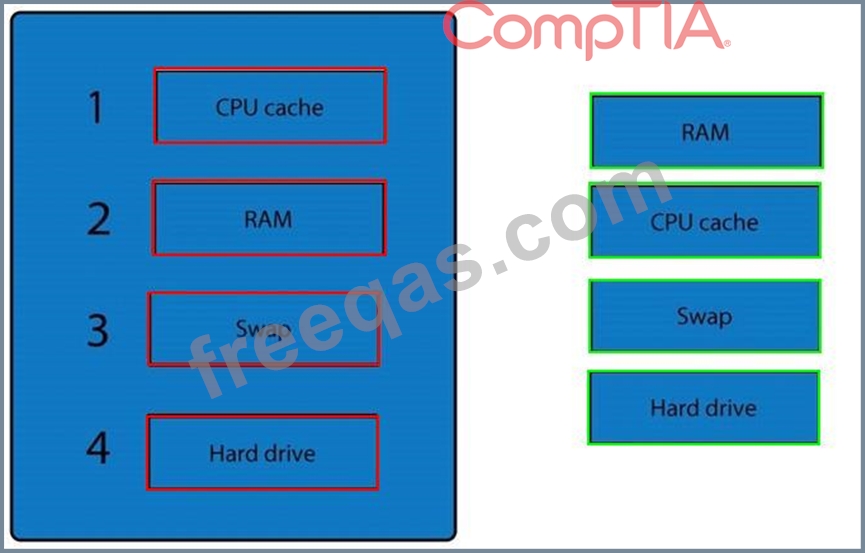
A forensic analyst is asked to respond to an ongoing network attack on a server. Place the items in the list below in the correct order in which the forensic analyst should preserve them.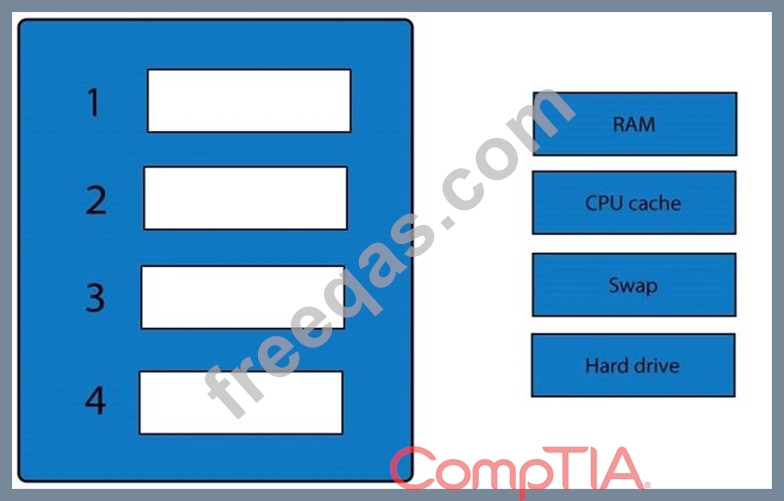
A security administrator is choosing an algorithm to generate password hashes. Which of the following would offer the BEST protection against offline brute force attacks?
A security engineer implements multiple technical measures to secure an enterprise network. The engineer also works with the Chief information Ofcer (CID) to implement policies to govern user behavior. Which of the following strategies is the security engineer executing?
A security analyst is reviewing the password policy for a service account that is used for a critical network service. The password policy for this account is as follows: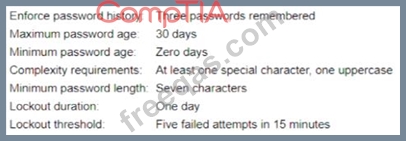
Which of the following adjustments would be the MOST appropriate for the service account?
