A security engineer implements multiple technical measures to secure an enterprise network. The engineer also works with the Chief information Officer (CID) to implement policies to govern user behavior. Which of the following strategies is the security engineer executing?
Which of the following concepts ensure ACL rules on a directory are functioning as expected? (Choose two.)
After a user reports slow computer performance, a system administrator detects a suspicious file, which was installed as part of a freeware software package. The systems administrator reviews the output below:
Based on the above information, which of the following types of malware was installed on the user's computer?
Upon learning about a user who has reused the same password for the past several years, a security specialist reviews the logs. The following is an extraction of the report after the most recent password change requirement: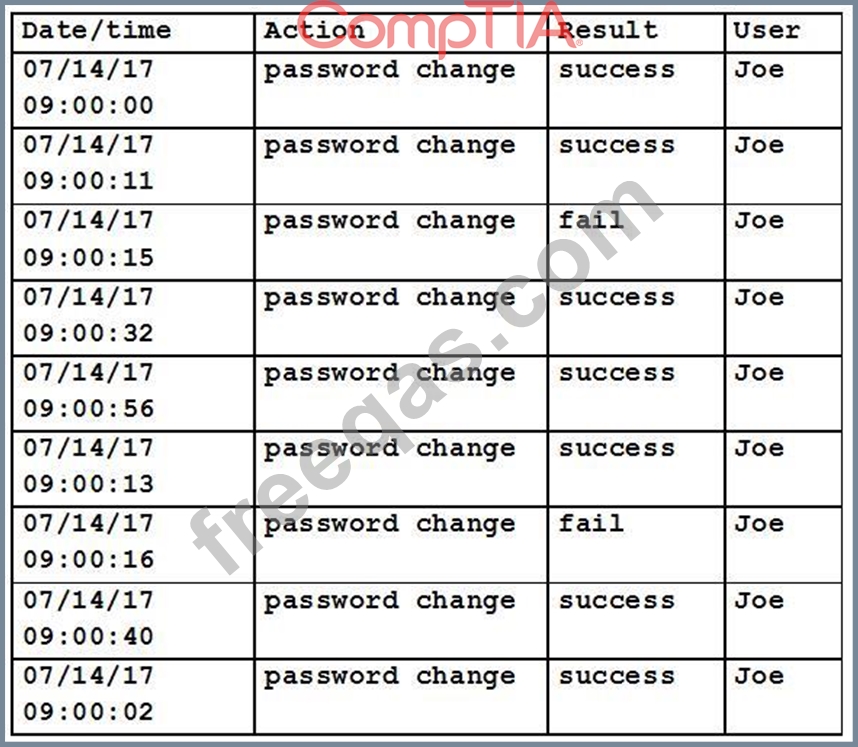
Which of the following security controls is the user's behavior targeting?
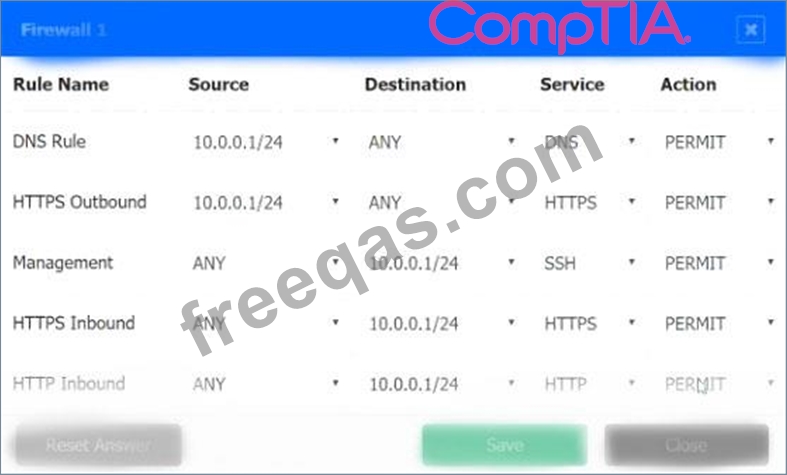
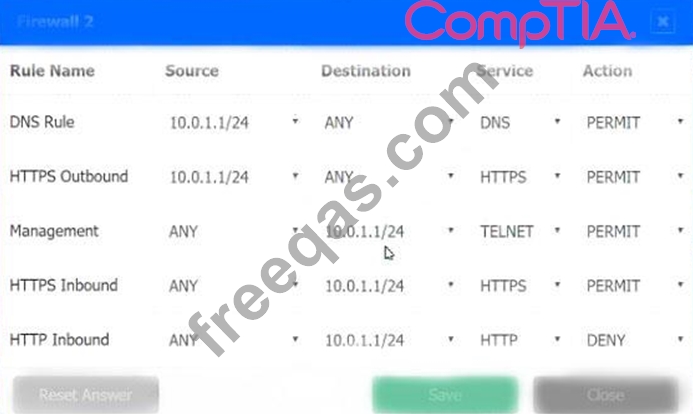
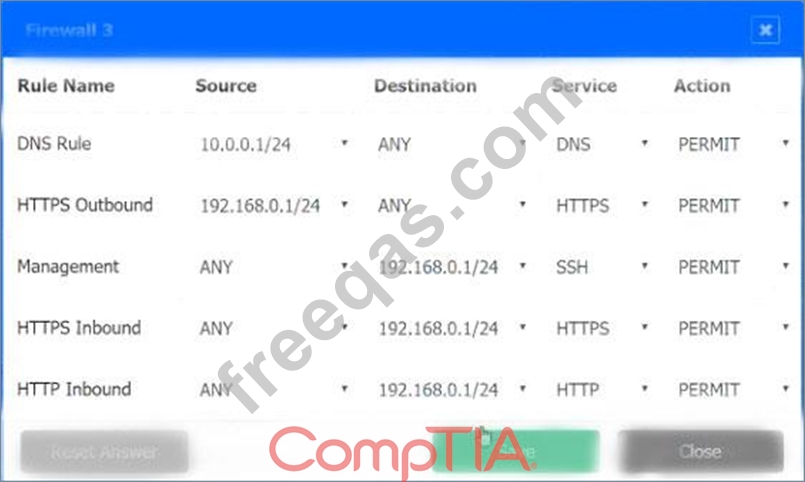
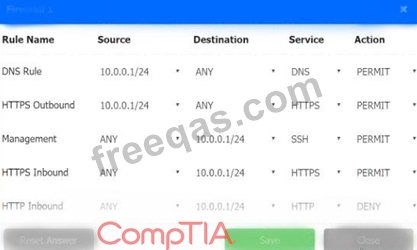
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
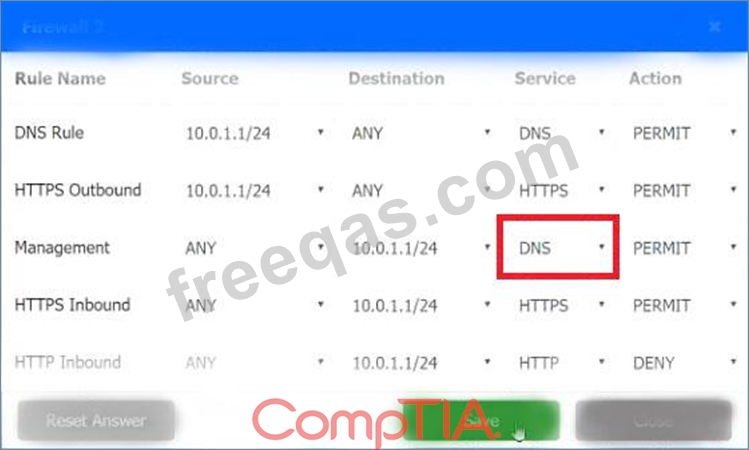
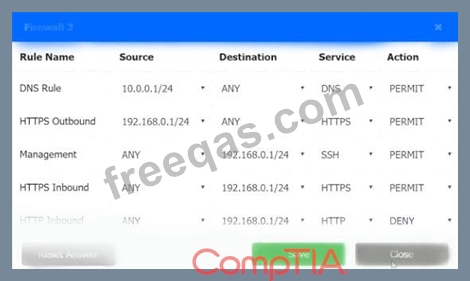
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.