An incident responder receives a call from a user who reports a computer is exhibiting symptoms consistent with a malware infection. Which of the following steps should the responder perform NEXT?
A new firewall has been places into service at an organization. However, a configuration has not been
entered on the firewall. Employees on the network segment covered by the new firewall report they are
unable to access the network. Which of the following steps should be completed to BEST resolve the
issue?
The network information for a workstation is as follows:
When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO).
A user clicked an email link that led to a website that infected the workstation with a virus.
The virus encrypted all the network shares to which the user had access. The virus was not detected or blocked by the company's email filter, website filter, or antivirus.
Which of the following describes what occurred?
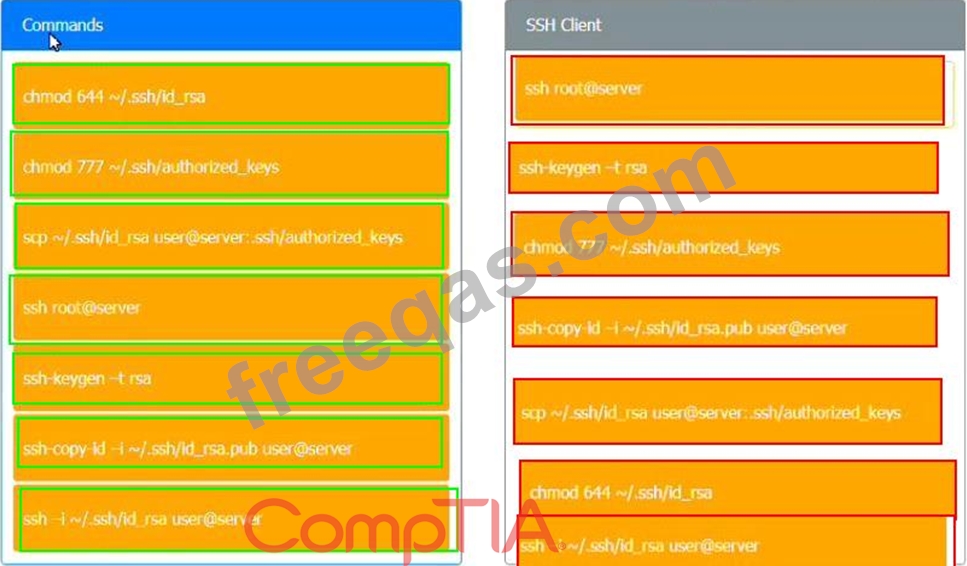
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.