A security administrator wants to implement strong security on the company smart phones and terminal servers located in the data center. Drag and drop the applicable controls to each asset types?
Instructions: Controls can be used multiple times and not all placeholders need to be filled. When you have completed the simulation, please select the Done button to submit.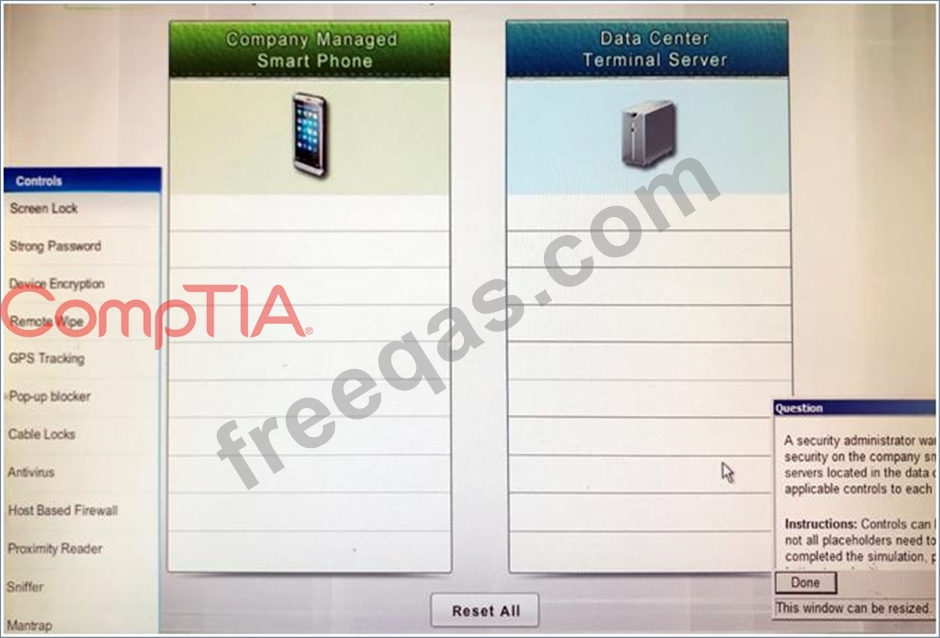

After disabling SSID broadcast, a network administrator still sees the wireless network listed in available networks on a client laptop. Which of the following attacks may be occurring?
The Chief Information Security Officer (CISO) is asking for ways to protect against zero-day exploits. The
CISO is concerned that an unrecognized threat could compromise corporate data and result in regulatory
fines as well as poor corporate publicity. The network is mostly flat, with split staff/guest wireless
functionality.
Which of the following equipment MUST be deployed to guard against unknown threats?
Company A agrees to provide perimeter protection, power, and environmental support with measurable goals for Company B, but will not be responsible for user authentication or patching of operating systems within the perimeter.
Which of the following is being described?
