A coding error has been discovered on a customer-facing website. The error causes each request to return confidential PHI data for the incorrect organization. The IT department is unable to identify the specific customers who are affected. As a result, all customers must be notified of the potential breach. Which of the following would allow the team to determine the scope of future incidents?
An organization wishes to provide better security for its name resolution services. Which of the following technologies BEST supports the deployment DNSSEC at the organization?
A technician has installed a new AAA server, which will be used by the network team to control access to a company's routers and switches. The technician completes the configuration by adding the network team members to the NETWORK_TEAM group, and then adding the NETWORK_TEAM group to the appropriate ALLOW_ACCESS access list. Only members of the network team should have access to the company's routers and switches.
Members of the network team successfully test their ability to log on to various network devices configured to use the AAA server. Weeks later, an auditor asks to review the following access log sample: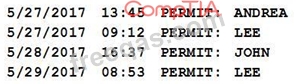
Which of the following should the auditor recommend based on the above information?
A member of the human resources department is searching for candidate resumes and encounters the following error message when attempting to access popular job search websites: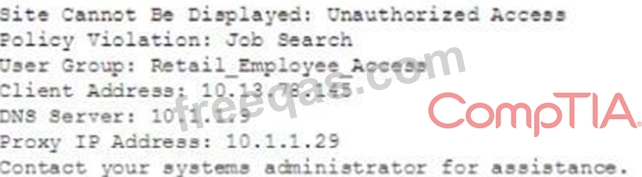
Which of the following would resolve this issue without compromising the company's security policies?
Which of the following types of penetration test will allow the tester to have access only to password hashes prior to the penetration test?
