A datacenter manager has been asked to prioritize critical system recovery priorities.
Which of the following is the MOST critical for immediate recovery?
A security administrator is given the security and availability profiles for servers that are being deployed.
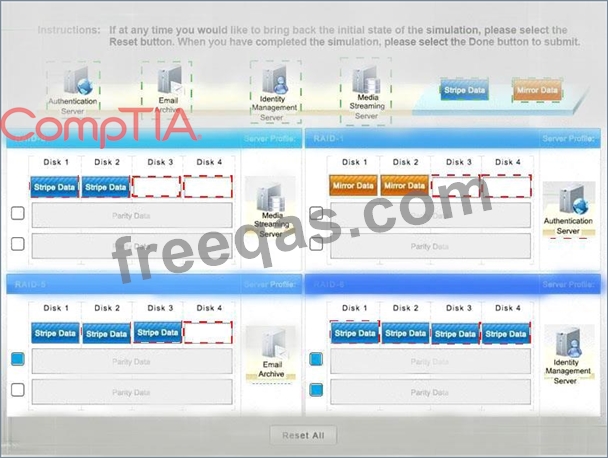
* Match each RAID type with the correct configuration and MINIMUM number of drives.
* Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements. Instructions:
* All drive definitions can be dragged as many times as necessary
* Not all placeholders may be filled in the RAID configuration boxes
* If parity is required, please select the appropriate number of parity checkboxes
* Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

A security analyst reviews the following output:
The analyst loads the hash into the SIEM to discover if this hash is seen in other parts of the network. After inspecting a large number of files, the security analyst reports the following: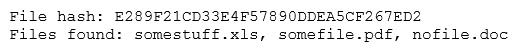
Which of the following is the MOST likely cause of the hash being found in other areas?
Ann, a new employee, received an email from an unknown source indicating she needed to click on the provided link to update her company's profile. Once Ann clicked the link, a command prompt appeared with the following output: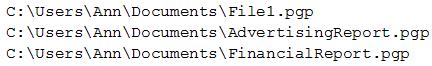
Which of the following types of malware was executed?
An organization has several production-critical SCADA supervisory systems that cannot follow the normal 30-day patching policy. Which of the following BEST maximizes the protection of these systems from malicious software?
